Many organizations are adopting hybrid IT environments that combine on-premises IBM i (AS/400) systems with cloud platforms to improve flexibility, scalability, and efficiency. At the core of these setups, IBM i (formerly AS/400) remains a trusted platform known for its reliability and strong security.
Over 100,000 businesses, including 70% of Fortune 100 companies, still use IBM i for critical operations. However, as hybrid systems expand, security challenges grow, especially with cloud-related issues and breaches involving multi-environment data.
From this blog, you will learn about the key risks associated with IBM i (AS/400) and the remedies in hybrid IT environments.
Understanding IBM i (AS/400) in Hybrid IT and Cloud Environments
Originally launched in 1988 as the AS400, IBM i is an all-in-one computing platform that combines hardware, operating system, database (DB2 for i), and built-in security in a single, reliable system. Its object-based design makes it less vulnerable to viruses and malware than traditional systems.
In 2025, IBM i (AS/400) continues to evolve with improved support for cloud integration and hybrid IT environments. Many organizations now use both on-premises IBM i systems and cloud platforms like IBM Power Virtual Server, Azure, and AWS to modernize their operations. This shift highlights the growing demand for IBM i hybrid cloud security solutions that ensure compliance and data protection.
This hybrid model helps businesses extend their existing systems while maintaining IBM i’s renowned 99.9% uptime. The platform now supports modern tools such as Python, Node.js, and REST APIs, enabling IBM i application modernization and secure API integrations with hybrid systems. Thus, it allows smooth integration with AI, machine learning, and DevOps workflows.
With the release of IBM i 7.6 (2024 – 2025), it remains a secure and powerful solution for modern enterprise needs.
Key Risks Associated with IBM i (AS/400) in Hybrid IT Environments
In hybrid IT ecosystems, IBM i security risks emerge from interconnected networks, shared resources, and multi-cloud exposure. Even though IBM i (AS/400) is known for its strong built-in security, it still faces several risks in hybrid IT environments.
As organizations connect on-premises systems with multiple cloud platforms, new vulnerabilities appear. Here are the key risks:
- Weak Security Configurations: Many IBM i (AS/400) systems still operate below the recommended QSECURITY level 40, leaving them exposed to unauthorized access and malware, a major issue highlighted in recent IBM i security audit reports.
- Unpatched Vulnerabilities: Critical flaws, such as CVE-2024-6387 (OpenSSH, score 8.1) and CVE-2024-27264 (privilege escalation, score 7.4), can enable attackers to execute code or gain higher-level access.
- IFS Vulnerabilities: The Integrated File System (IFS) is a common entry point for ransomware, often spreading through shared drives connected to infected Windows systems.
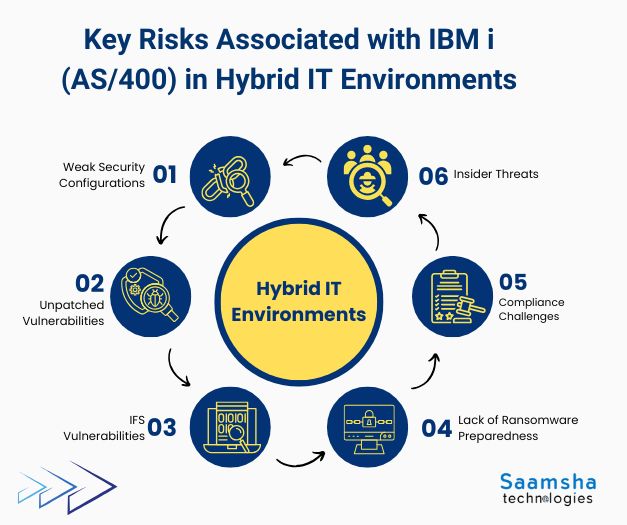
- Lack of Ransomware Preparedness: Less than 50% of businesses have formal response plans, and 34% take over a month to fully recover from attacks.
- Compliance Challenges: Meeting standards like GDPR, HIPAA, PCI-DSS, and SOX is increasingly difficult in hybrid environments. In 2024, 27% of public cloud users reported security incidents related to compliance gaps.
- Insider Threats: 83% of organizations experienced at least one insider attack in 2024, highlighting growing risks from within.
Don’t let security vulnerabilities compromise your critical business operations. Saamsha Technologies brings expertise to help you implement robust security measures. Secure AS400 operating systems in hybrid IT environments and safeguard your enterprise data with us!
Remedies and Best Practices to Reduce IBM i (AS/400) Security Risks in Hybrid IT Environments
Securing IBM i (AS/400) in hybrid IT environments requires a layered security approach that covers prevention, detection, and recovery. Here are the key steps companies should follow:
- Strengthen Access Controls
Raise QSECURITY settings to level 40 or higher and apply the least privilege rule. Remove unnecessary authorities like *ALLOBJ and *SECADM. Enable multi-factor authentication (MFA) for admin access and adopt a Zero Trust model that verifies every login or connection, regardless of location.
- Encrypt All Data
Use DB2 FIELDPROC for field-level encryption and apply AES (NIST-approved) encryption to secure data stored in databases, IFS files, and backup media. For data transfers between on-premises and cloud, ensure end-to-end encryption to protect sensitive information.
- Segment Networks and Restrict Access
Reduce attack surfaces by controlling IFS access with exit point programs that monitor directory visibility. Configure firewalls, IDS/IPS, and VPNs to secure data traffic and prevent unauthorized access.
- Enable Continuous Monitoring
Activate IBM i’s built-in logging and integrate it with AI-based SIEM tools for real-time analysis. These systems can detect and alert on unusual file access, network anomalies, or suspicious activity before threats escalate.
- Ensure Reliable Backups and Recovery
Maintain tested backup and disaster recovery plans. Restrict direct access to backup systems to stop ransomware from encrypting or deleting recovery data. For instance, you can leverage IBM PowerHA or BRMS solutions to automate backup management and reduce recovery time objectives (RTO).
- Keep Systems Updated
Apply security patches regularly. The 2024 IBM i (AS/400) updates addressed several vulnerabilities, which show the importance of timely patch management.
- Conduct Audits and Training
Perform regular internal and external security audits to identify weaknesses. Train employees to spot phishing and social engineering attacks, which often trigger ransomware infections.
Final Words
Securing IBM i (AS/400) systems in hybrid IT environments is crucial in 2025. With breaches averaging $4.35 million and 82% involving cloud data, robust protection is vital. Properly configured AS400 security offers strong defense through higher QSECURITY levels and field-level encryption.
Organizations should enforce Zero Trust, segment networks, apply AI-driven monitoring, test recovery plans, and train staff. AS400 system’s enhanced security and cloud integration make it future-ready.
Partnering with an IBM i managed service provider like Saamsha Technologies ensures continuous monitoring, compliance readiness, and seamless hybrid IT performance, keeping businesses secure and competitive in a high-risk landscape.
Ready to transform your legacy IBM i security architecture while maintaining business continuity? We specialize in AS400 modernization, integration, and security enhancement services across manufacturing, banking, retail, and healthcare sectors. Contact now!



