In August 2025, Salesloft’s Drift chatbot service attack revealed a critical truth. Linking legacy systems like IBM i to modern web applications without strong security makes them liabilities. Attackers stole OAuth and refresh tokens and other keys and breached 700+ organizations.
While IBM i (AS/400) handles core business data in sectors such as finance and government, organizations modernizing by exposing it via web APIs inadvertently create new attack surfaces. In India, the average cost of a data breach has surged to INR 220 million in 2025.
Why IBM i (AS/400 Operating System) Security Matters More Than Ever?
IBM i was built initially for secure, closed, internal networks, while web apps operate in open, high-risk environments where attackers constantly seek weaknesses. Without a strong security design, linking the two can lead to serious breaches.
Cloudflare’s 2024 State of Application Security Report reveals that:
- Companies use about 47 third-party scripts per application.
- API traffic now makes up 58% of all online activity.
- Many organizations have 33% more public APIs than they realize, so-called shadow APIs that lack proper security controls.
For IBM i teams exposing business functions via REST APIs, these stats highlight a real danger: unprotected endpoints can give attackers direct access to critical systems. Attackers began exploiting newly disclosed vulnerabilities within 22 minutes.
Preventive architecture, strong encryption, strict authentication, and active monitoring are essential to keep these legacy systems safe in today’s web-connected world.
Ready to strengthen your IBM i (AS/400) REST APIs without compromising performance? Saamsha Technologies helps organizations modernize IBM i integrations with enterprise-level encryption, authentication, and security architecture. Partner with us now!
The Technical Foundation: TLS 1.3 and Modern Encryption
Securing data exchange between IBM i systems and web applications begins with robust encryption. The latest standard, Transport Layer Security (TLS) 1.3, used by over 70% of websites, establishes secure connections faster than TLS 1.2, improving real-time API performance by about 25%. It also includes Perfect Forward Secrecy (PFS), ensuring that even if encryption keys are later compromised, past data remains protected.
To strengthen security, organizations should pair TLS 1.3 with AES-256 encryption for stored data. However, encryption alone is insufficient. Nearly two-thirds of organizations still depend on outdated Web Application Firewalls (WAFs) built for websites rather than APIs, leaving integrations vulnerable to modern threats like endpoint discovery, credential theft, and authentication hijacking.
IBM i provides native tools such as the Digital Certificate Manager (DCM), Exit Programs, and Authority Collection for granular access control. When integrated with web-layer security, these ensure compliance with IBM i’s trusted architecture while maintaining secure external connectivity.
Concerned that hidden APIs might put your IBM i systems at risk? Our security-first approach uncovers unmonitored endpoints and uses real-time anomaly detection to safeguard your legacy systems. Connect with Saamsha Technologies now!
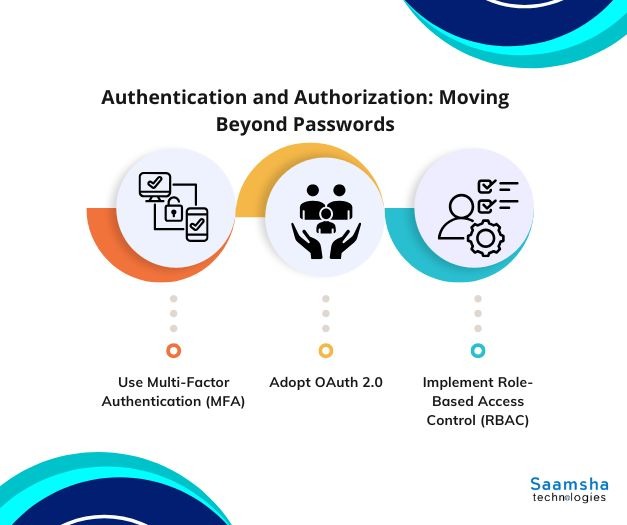
Authentication and Authorization: Moving Beyond Passwords
IBM i (AS/400)’s Integrated Web Services (IWS) lets teams quickly expose RPG, COBOL, or SQL programs as REST APIs, often in just minutes. However, creating APIs without strong security is like leaving your database keys out in the open.
The OWASP API Security Top 10 lists Broken Object Level Authorization (BOLA) as the most common API flaw, found in about 40% of attacks.
To secure IBM i-web integrations:
- Use Multi-Factor Authentication (MFA): Every service account should require MFA. Passwords alone aren’t enough in today’s credential-theft landscape.
- Adopt OAuth 2.0: Replace basic authentication with OAuth 2.0 so third-party apps use temporary, revocable tokens instead of direct IBM i (AS/400) credentials.
- Implement Role-Based Access Control (RBAC): Apply the least-privilege principle, give each app access only to what it needs.
Moreover, recent breaches prove the risk. The Oracle Cloud breach (Mar 2025) and Jaguar Land Rover breach both stemmed from weak authentication controls and exposed credentials.
Continuous Monitoring and Anomaly Detection
Between 2024 and 2025, AI-driven anomaly detection reduced API breach detection time from 45 days to just minutes, a critical improvement for IBM i systems handling financial or customer data. For IBM i systems handling financial or sensitive data, this kind of real-time monitoring has become essential, not optional.
Meanwhile, IBM’s new REST-based security APIs simplify TLS certificate management by automating renewals and updates.
They also allow certificates to be exported in DER, PEM, or PKCS12 formats, making it easier to maintain secure, up-to-date encryption channels and enable trusted authentication between IBM i and modern web applications.
Stop relying on outdated firewalls for API security. Saamsha delivers API-specific threat detection and continuous monitoring tailored for IBM i modernization to protect your critical business data against attacks.
Protecting the Integration Layer
Organizations connecting IBM i (AS/400) systems with web applications must follow key security steps:
- Use TLS 1.3 for encryption, allowing TLS 1.2 only when absolutely required.
- Enable multi-factor authentication (MFA) for all service accounts.
- Apply OAuth 2.0 for external access instead of basic authentication.
- Keep a complete API inventory, including hidden or shadow APIs.
- Use API-specific security rules, not just traditional web firewalls.
- Encrypt all data in transit and at rest with AES-256.
- Maintain audit logs and enable real-time alerts for suspicious API activity.
For critical IBM i systems, delayed detection means more prolonged exposure, damaged customer trust, and potential regulatory fines.
Final Thoughts
Securing data exchange between IBM i (AS/400) systems and web applications bridges the gap between reliable legacy technology and modern cybersecurity needs. AS/400 system’s strength and stability only matter if protected by strong encryption, authentication, and continuous monitoring.
This integration should be treated as a strategic security priority, not a technical add-on. From the start, organizations should use TLS 1.3 encryption, OAuth 2.0 authorization, multi-factor authentication (MFA), and API-specific monitoring to detect threats early.
Investing in a secure data exchange framework now is far cheaper and safer than paying the cost of a future data breach.
So, partner with Saamsha Technologies to modernize your IBM i (AS/400) systems securely. Strengthen encryption, authentication, and monitoring to protect critical data while enabling seamless web integration.



